The second involves the use of third-party texting apps that can be used to schedule text messages on any Android smartphone. As an alternative you can use the Legacy Google Voice interface and set a ring schedule for each phone linked to your account.
 This Gmail Hack Lets You Schedule Send Sms Text Messages In Three Steps
This Gmail Hack Lets You Schedule Send Sms Text Messages In Three Steps
GV Android App AddEdit Contacts.

Google voice schedule text. A Voice number works on smartphones and the web so you can place and receive calls from anywhere Save time stay connected From simple navigation to voicemail transcription Voice makes it easier than ever to save time while staying connected. This will work for. GV has always been a bit of a pain adding someone as a contact from an incoming text or call.
The only requirements are an IFTTT account linked to the necessary apps IFTTT will request. To do so visit the following website. Click the settings wheel in the top right corner.
If you use Gmail and Google Voice youre in luck all you need to do is setup Boomerang an extra service for gmail that schedules emails to be sent or read later but with some more setup it can also be applied to scheduling texts. It is a helpful feature that was a long-time coming but many users are enjoying it. Configure your Google Voice account to forward your messages to your email addresss.
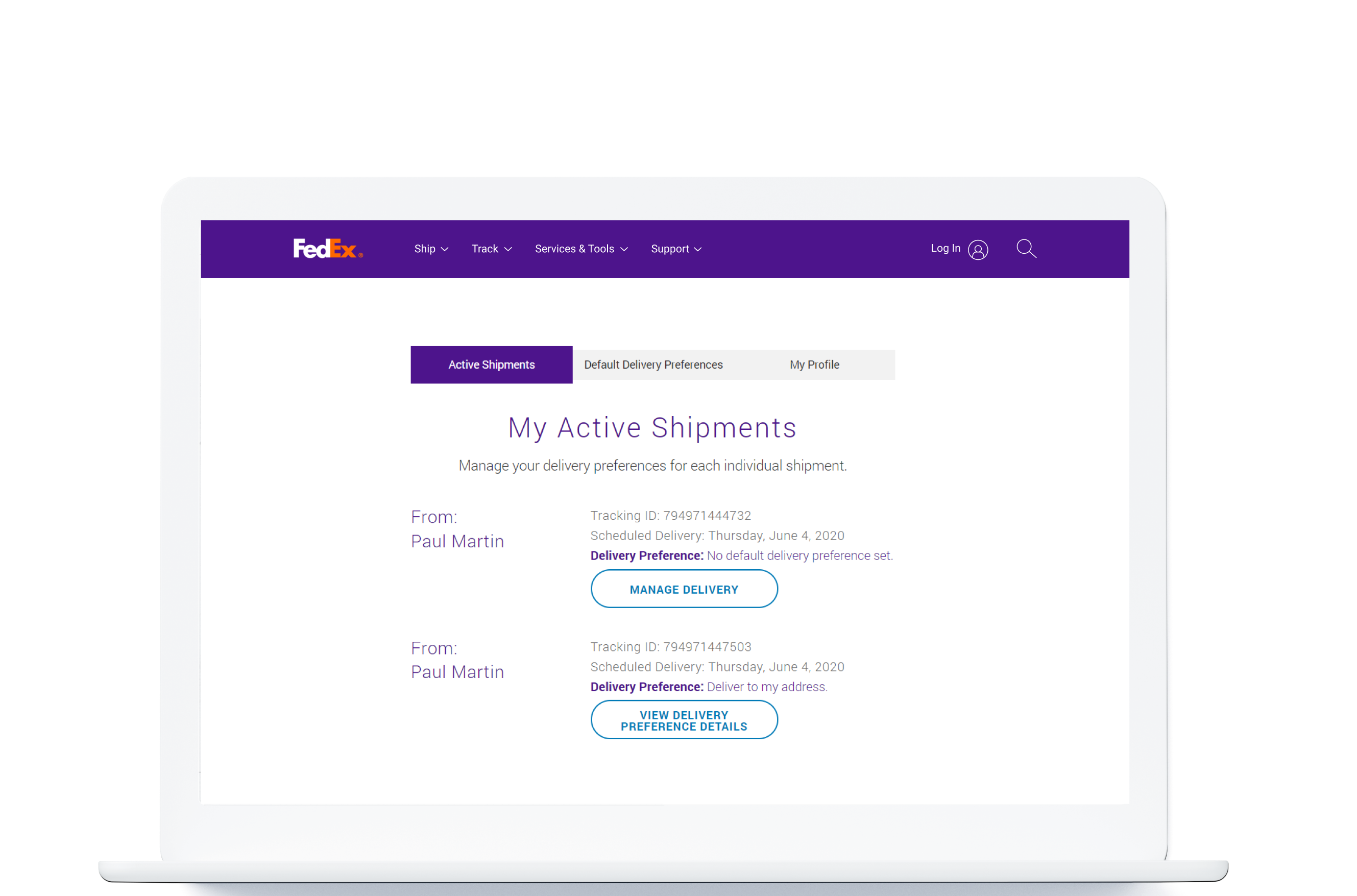
Once the app is opened youre greeted with a basic page that shows your scheduled text messages. At the bottom of the screen youll want to click the phone bubble to sign into your Google Voice account. Near the bottom right remember to click the settings button for making Google Voice your preferred message type.
GV doesnt seem to have this feature and suddenly I am starting to feel unhappy with GV. Its even worse now as there is no way to actually copy the phone number and paste it into a New Contact. If you use Gmail and Google Voice youre in luck all you need to do is setup Boomerang an extra service for gmail that schedules emails to be sent or read later but with some more setup it can also be applied to scheduling texts.
Google released a scheduling function for its Gmail service in April. We have included both these. Click the Phones tab to see all of the phones your Google Voice number forwards to.
The first is to use the built-in functionality that the Google Messages app and certain Android OEMs like Samsung Xiaomi and LG offer. To schedule an SMS on Android you can use two methods. Setup a Boomerang account.
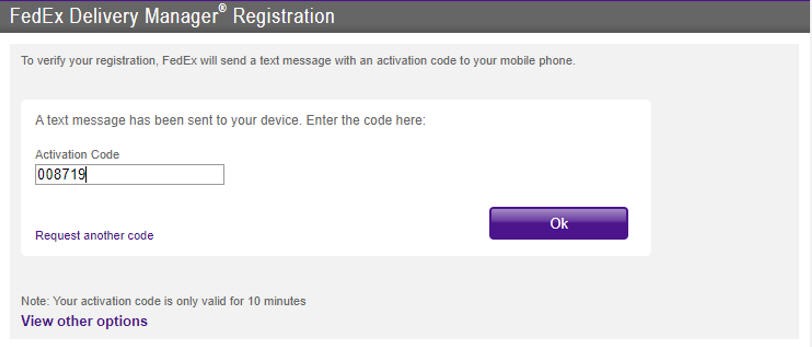
This IFTTT applet can be used to schedule a text message when a Google Calendar event is triggered. So what were going to do is configure Google Voice to send an email to Gmail when it gets a text. Select the one you want set office hours for and click Edit Now youll see a section called Ring Schedule.
If you dont know which network the recipient is on or if youd rather use your Google Voice account here is how you can use Google Voice to schedule text messages. Today I found out that regular texting apps on Android have a feature where you can schedule a text to be sent at a time of your choice. Plus I wanted to schedule texts from my computer instead of pecking on a tiny keyboard.
Here is the link to Google Voice Settings page. To see calling rates for your work or school sign in to your account. I use GoogleVoice GV for texts and have been very happy with it.
When Gmail gets that email based on matching filter selection rules it will automatically reply. Youre not signed in to your account. One way to do this is to schedule a message from Gmail to a text recipient for example.
It required more steps than should ever be needed. Google Voice calling rates Rates may change at any time. If you have a Google Voice number.