See Whos Our Best Rated Antivirus Software. 360 Total Security Premium installs quickly and is a.
 App Review 360 Security Lite Don T Get Stuck In Your Phone Blog Of Himanshu Sheth On Technology Entrepreneurship And Business
App Review 360 Security Lite Don T Get Stuck In Your Phone Blog Of Himanshu Sheth On Technology Entrepreneurship And Business
Let Us Help You Find The Perfect Antivirus.
360 security app. These smart tools include. Norton 360 for Mobile provides powerful protection for your mobile device. A freeware antivirus and general online protection application.
360 Total Security protects you from various kinds of malware programs using multiple anti-virus engines such as 360 Cloud Scan Engine 360 QVMII AI Engine Avira and Kunpeng. See Whos Our Best Rated Antivirus Software. Protect Your Computer From Viruses Malware.
By Qihoo 360 Technology 360 Total Security is an unified solution for your PC security and performance. Protects not only your phone but also your privacy. Mobile Security and enjoy it on your iPhone iPad and iPod touch.
It can also block hitherto-unknown malware programs using behavior monitoring. Secure your apps and avoid turning them into an attack vector with App Shielding. The software carries out essential functions with ease and has a clean user interface that has a modern yet simple and intuitive feel.
As part of the tool you get a comprehensive PC maintenance suit and a power-packed security tool. Let Us Help You Find The Perfect Antivirus. Ad When your app is released its security will be fiercely tested.
Its cloud-based technology quickly detects the latest ransomware variants in real time. Protect your apps now. At the core of the scan engine and AI engine 360 Total.
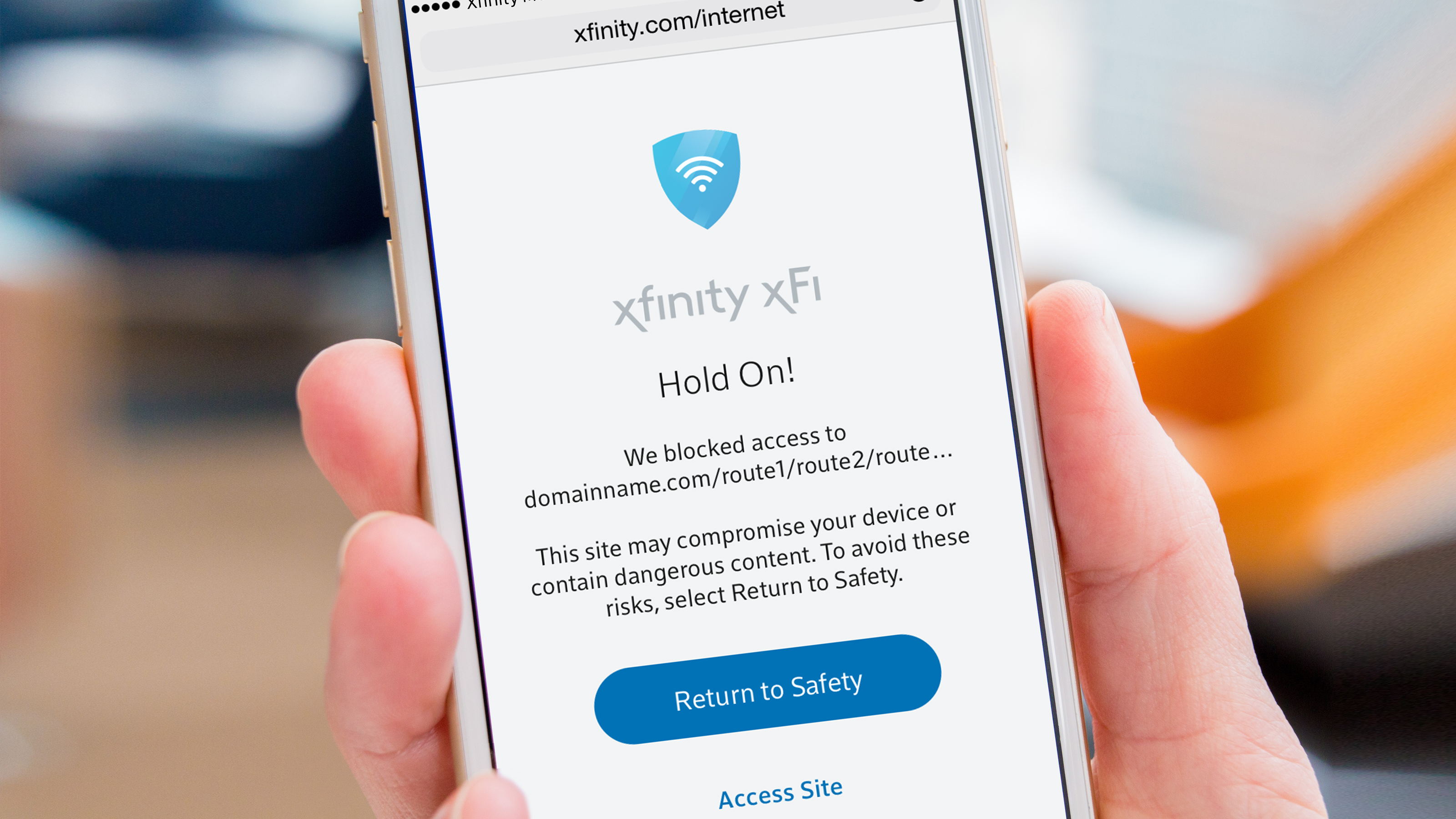
- Dedicated VPN - Safe Browser no log browser - Passcode Protected Photo Vault - Passcode Protected Password Keeper - Motion-Controlled Anti-theft Features - VPN. 360 Total Security is an anti-malware and antivirus program produced by Chinese developer Qihu. The description of 360 Total Security Antivirus App 360 Total Security Antivirus upgraded to the whole new 360 Total Security Antivirus and redefined the scalp of Phone Security.
Over 200 million users trust 360 Mobile Security as their all-in-one antivirus and junk cleaning app. Protect Your Computer From Viruses Malware. - FULL CHECK checks the overall condition of your computers health and safety.
Protect your apps now. Download Norton 360. Protecting your PC is a day-to-day essential as its becoming ever more important to have complete protection in order to keep your computer running well.
Trusted by 200 million users 360 Security is the all-in-one power cleaner smart speed booster and antivirus app that optimizes your background apps memory storage junk files battery power. The program protects your PC from viruses ransomware phishing spyware and malware attacks. Trusted by 200 million users Safe Security is the all-in-one power cleaner smart speed booster and antivirus app that optimizes your background apps memory storage junk files battery power.
Protect your mobile device with 360 Security a top of the line free security app designed to protect your Android phone against the latest virus malware system vulnerabilities and privacy risks. Secure your apps and avoid turning them into an attack vector with App Shielding. One of the advantages of 360 Total Security is its reliance on multiple antivirus engines which allows for better detection of malware.
Ad 2021s Best Antivirus Review. This app optimizes your background apps scans for junk files battery power and memory space. The app also cleans application caches and junk files from your system Increases the available storage space on SD card and boosts your Android phone for free.
Once it stops scanning you often have a more efficient smartphone and at the same time you defend your device from viruses and Trojans. Using APKPure App to upgrade 360 Total Security Antivirus fast free and save your internet data. Ad 2021s Best Antivirus Review.
Developed by Qihoo a prominent company in China 360 Total Security is a free antivirus program. It monitors for cyberattacks attempting to leverage OS vulnerabilities for malicious purposes and automatically checks for the latest security patches and OS updates. With Full Check you can examine the overall condition of.
Ad When your app is released its security will be fiercely tested. 360 Total Security displays your computer protection status startup time and disk usage also offers quick access to key features including. QIHUs 360 Total Security Premium is a quality antivirus security product.
360 Mobile Phone Security offers you 5 powerfully smart cyber security tools to protect your data on iPhone iPad every day.