Taking action at now are often considered critical. And in this face on particular hackers can take advantage off ascent 0159.
 Leveraging The Human To Break The Cyber Kill Chain
Leveraging The Human To Break The Cyber Kill Chain
The term kill chain is adopted from the military which uses this term related to the structure of an attack.

Cyber kill chain model. In this article we will discuss what the cyber kill chain is and what its steps are. This model is defender centric. So many models to choose.
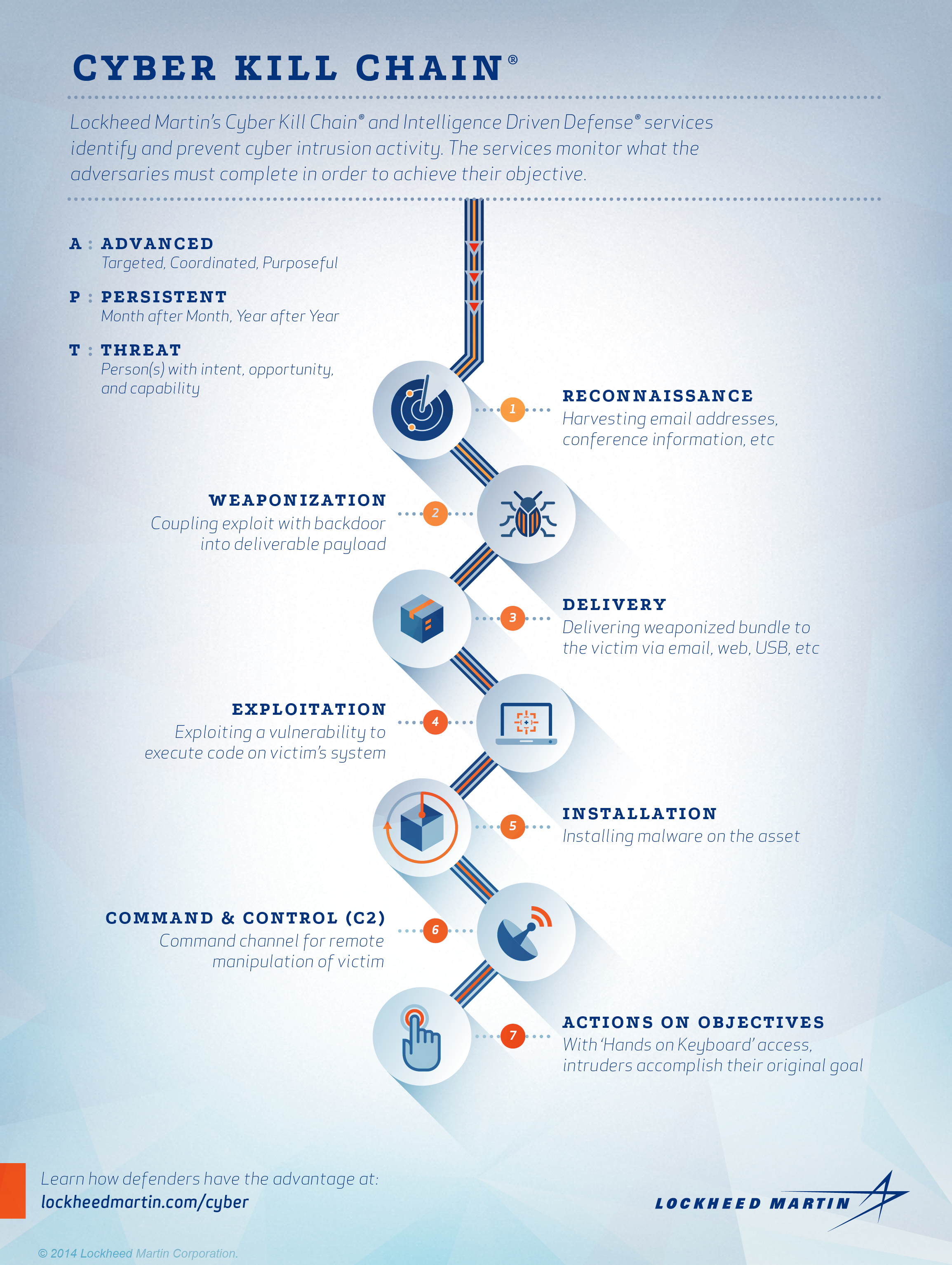
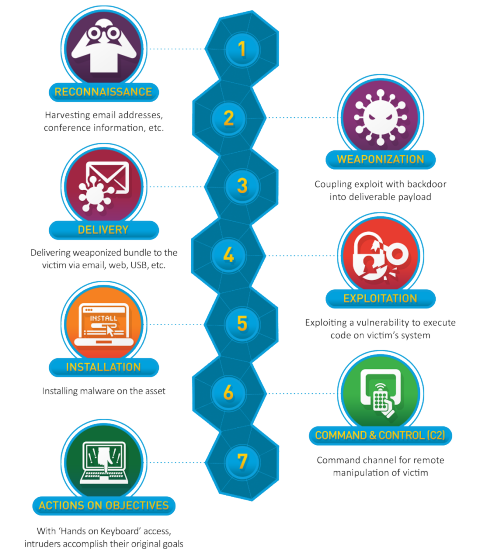
The first step is reconnaissance which means gathering data and intelligence on target organization. What is the Cyber Kill Chain Model. Cyber Kill Chain.
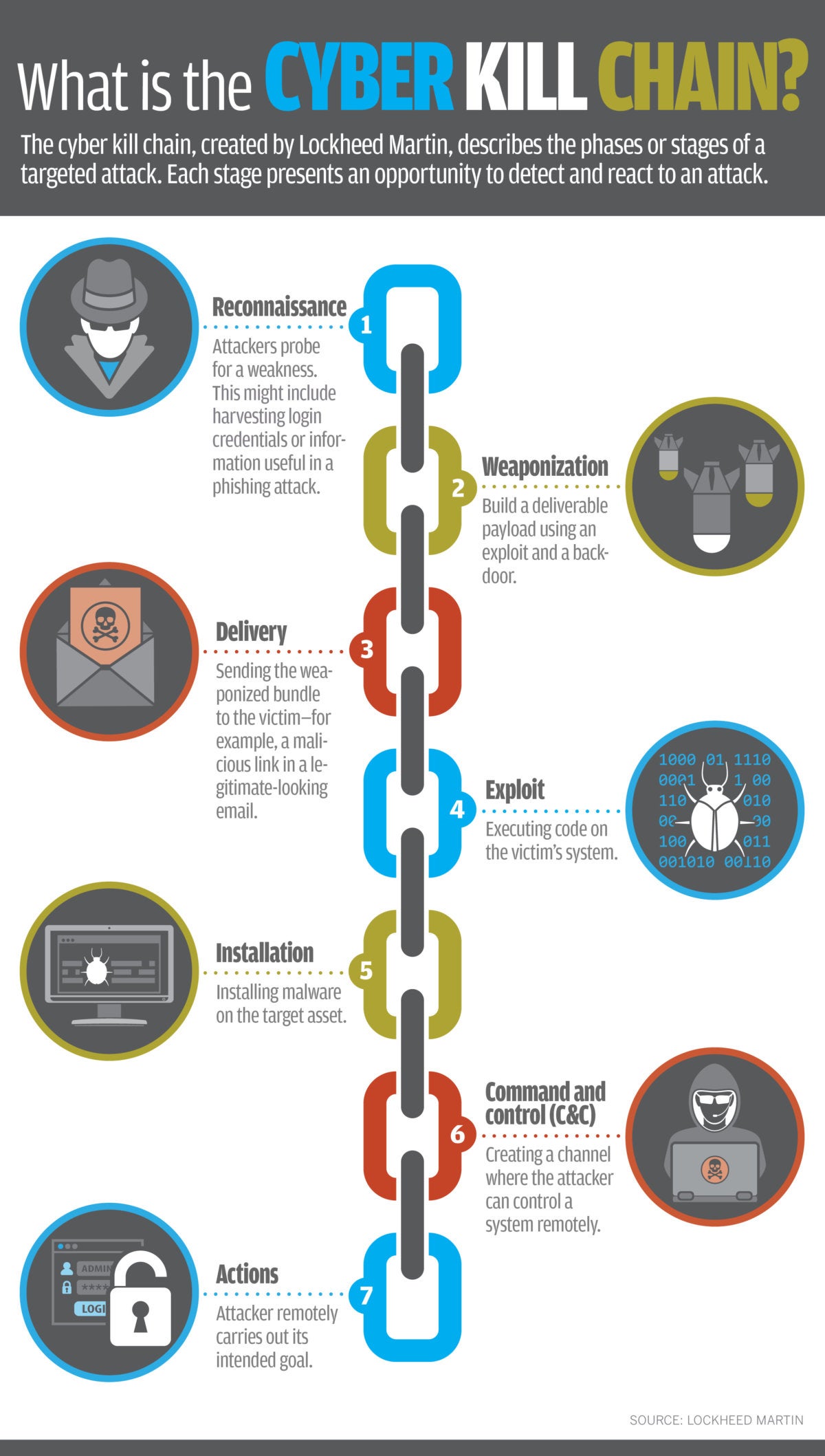
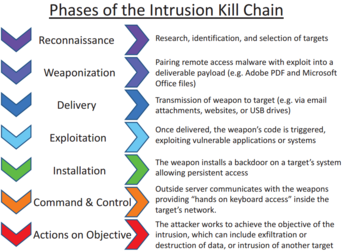
At the cyber kill chain in this the installation stage of a foreign access Trojan or backdoor on the victim system allows the adversary to take care of persistence inside the environment. The cyber kill chain is a process composed off seven steps that we will see briefly in this light. Lockheed Martin derived the kill chain framework from a military model originally.
Developed by Lockheed Martin the Cyber Kill Chain framework is part of the Intelligence Driven Defense model for identification and prevention of cyber intrusions activity. Its designed for defenders to improve their defenses by analyzing an attackers playbook the kill. The model identifies what the adversaries must complete in order to achieve their objective.
Nevertheless it is advisable to keep the definition of the defense strategy very abstract for the first two steps in order to maintain and use the Cyber Kill Chainprocess. This means that to frustrate the objectives of the attacker the defender must disrupt one element of. These three seminal cybersecurity and intrusion analysis models are not conflicting in fact they are complementary you use all three together.
The purpose of the model is to better understand the stages an attack must go through to conduct an attack. Slide 2 The cyber kill chain is a sequence of stages required for an attacker to successfully infiltrate a network and exfiltrate data from it. The kill chain helps us understand and combat ransomware security breaches and advanced persistent attacks APTs.
The cyber kill chain is essentially a cybersecurity model created by Lockheed Martin that traces the stages of a cyber-attack identifies vulnerabilities and helps security teams to stop the attacks at every stage of the chain. The Cyber Kill Chain applies the century-old military kill chain model to a cyberattack. Diamond Model Kill Chain and MITRE ATTCK Oh My.
Similar in concept to the militarys model it defines the steps used by cyber attackers in todays cyber-based attacks. Cyber intrusions are the worst nightmare of many of us. This framework was introduced in 2009 by Lockheed Martin in their paper entitled Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains.
Luckily you do not have to choose. In 2011 Lockheed Martin released a paper defining a Cyber Kill Chain. The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data.
The Cyber Kill Chain offers a comprehensive framework as a part of the Intelligence Driven Defense model. The cyber kill chain CKC is a classic cybersecurity model developed by the computer security incident response CSIRT team at Lockheed Martin. At the end the challenge is to find an appropriate way of handling potential definition flaws in the Cyber Kill Chain model.
Each stage demonstrates a. Kill chain is a term originally used by the military to define the steps an enemy uses to attack a target. Installing malware on the asset requires end-user participation by unknowingly enabling the malicious code.
 The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
 The Unified Kill Chain Part 2 Mitigate Cyber
The Unified Kill Chain Part 2 Mitigate Cyber
 What Is The Cyber Kill Chain Why It S Not Always The Right Approach To Cyber Attacks Cso Online
What Is The Cyber Kill Chain Why It S Not Always The Right Approach To Cyber Attacks Cso Online
 What Is A Cyber Kill Chain And How It Works Stages And Examples
What Is A Cyber Kill Chain And How It Works Stages And Examples
 Deconstructing The Cyber Kill Chain
Deconstructing The Cyber Kill Chain
 What Is The Cyber Kill Chain And How To Use It Effectively Varonis
What Is The Cyber Kill Chain And How To Use It Effectively Varonis
 Eventtracker Enterprise And The Cyber Kill Chain Netsurion
Eventtracker Enterprise And The Cyber Kill Chain Netsurion
 What Is The Cyber Kill Chain And How To Use It Effectively Varonis
What Is The Cyber Kill Chain And How To Use It Effectively Varonis
 Lockheed Martin Cyber Kill Chain Ckc 22 Seven Steps The Part That Download Scientific Diagram
Lockheed Martin Cyber Kill Chain Ckc 22 Seven Steps The Part That Download Scientific Diagram
 What Is Cyber Kill Chain And It S 7 Phases Infosavvy Security And It Management Training
What Is Cyber Kill Chain And It S 7 Phases Infosavvy Security And It Management Training
 Cyber Kill Chain Lockheed Martin
Cyber Kill Chain Lockheed Martin
 What Are The Different Phases In A Successful Cyber Kill Chain
What Are The Different Phases In A Successful Cyber Kill Chain
 What Is A Cyber Kill Chain And How It Works Stages And Examples
What Is A Cyber Kill Chain And How It Works Stages And Examples

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.