Force-authorizedDisables 8021X authentication on the interface and causes the port to transition to the authorized state without any authentication exchange required. 8021X security is a way of controlling access to a logical network from a physical one.
 Ieee 802 1x Simple English Wikipedia The Free Encyclopedia
Ieee 802 1x Simple English Wikipedia The Free Encyclopedia
The purpose of 8021x is to accept or reject users who want full access to a network using 8021x.
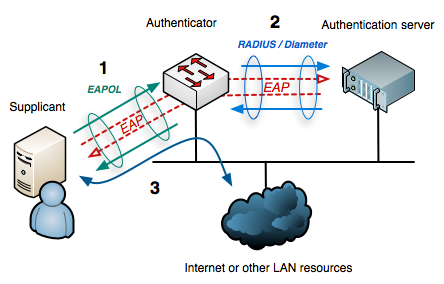
802.1 x security. All clients who want to join the logical network must authenticate with the server a router for example using the correct 8021X authentication method. IEEE 8021X dot1x uses the Extensible Authentication Protocol EAP to exchange messages during the authentication process. Printer then reconnects and I can printout whatever is in the queue.
It is a security protocol that works with 80211 wireless networks such as 80211bgn as well as with wired devices. Details of 8021x Authentication. The IEEE 8021X standard defines how to provide authentication for devices trying to connect with other devices on LANs or wireless LANs.
The purpose of 8021x is to accept or reject users who want full access to a network using 8021x. You must also configure port security on the port by using the switchport port-security interface configuration command. AutoEnables 8021X authentication on the port and causes it to transition to the authorized or unauthorized state based on the 8021X authentication exchange between the device and the client.
When key network settings are omitted in the configuration process which they commonly are devices lose the security benefits of 8021X and put their network at serious risk. 8021x Security Why IT Professionals Arent Overlooking 8021x Network Authentication For VDI While we all can agree that 8021x Network Authentication is not brand new we all can also agree that its presence and use continue to play an even more critical role when it comes to network security in your computer environment - including. What is 8021X EAP Security.
EAP IETF RFC 2284 is a highly pliable standard. The standard authentication protocol used on encrypted networks is Extensible Authentication Protocol EAP which provides a secure method to send identifying information over-the-air for network authentication. 8021X can be a difficult protocol to configure and manage especially for end users.
HP Officejet Pro 8625 routinely disconnects from network and I have to go to the printer Network Setup Reset 8021x Security and reset it. With the multiple-hosts mode enabled 8021X authenticates the port and port security manages network access for all MAC. Put another way firewalls help protect from attacks originating outside the network and 8021x helps protect from attacks originating within the network.
8021x encompasses the range of EAP authentication methods including MD5 TLS TTLS LEAP PEAP SecurID SIM and AKA. All NETGEAR ProSAFE Layer 2 and Layer 3 switches support this authentication. It is a security protocol that works with 80211 wireless networks such as 80211g and 80211b as well as with wired devices.
Company-Wide IEEE Codes Subscription Available. Using 8021X with Port Security. Then within a couple minutes it disconnects from the Network again.
Ad Search and Buy IEEE Standards. 8021X overview 8021X is a port access protocol for protecting networks via authentication. Here is a video of how to manually setup 8021X on a Windows device.
In a wired Ethernet LAN EAPoL Extensible Authentication Protocol EAP over LAN is used to transport EAP packets between Supplicant and. 8021X is the standard that is used for passing EAP over wired and wireless Local Area Networks LAN. Ad Search and Buy IEEE Standards.
You can enable an 8021X port for port security by using the dot1x multiple-hosts interface configuration command. 8021X security is the name of the IEEE standard for port-based Network Access Control PNACIt is also called WPA Enterprise. As a result this type of authentication method is extremely useful in the Wi-Fi environment due to the nature of the medium.
Company-Wide IEEE Codes Subscription Available. 8021x network security provides protection from someone walking in connecting a rogue device to your network and releasing a virus malware or a man-in-the-middle attack.
