As the de facto standard for encryption key management HSMs provide a full complement of features and administrative functionality including. Because this data is sensitive and business critical you need to secure access to your managed HSMs by allowing only authorized applications and users to access it.
 New Ncipher Hsm As A Service Delivers High Assurance Security For Organizations Adopting Cloud First Strategies Business Wire
New Ncipher Hsm As A Service Delivers High Assurance Security For Organizations Adopting Cloud First Strategies Business Wire
A cloud-hosted key management service that lets you manage symmetric and asymmetric cryptographic keys for your cloud services the same way you do on-premises.

Hsm key management. FIPS 140-2 Compliant Key Management - The highest standard for encryption key management is the Federal Information Processing Standard FIPS 140-2 issued by NIST. This article provides an overview of the Managed HSM access control model. Groups and Policy For my Enterprise Key Environment.
Azure Key Vault Managed HSM is a fully managed highly available single-tenant standards-compliant cloud service that enables you to safeguard cryptographic keys for your cloud applications using FIPS 140-2 Level 3 validated HSMs. Using the same FIPS 140-2 compliant technology that is in our hardware security module HSM and in use by over 3000 customers Alliance Key Manager for VMware brings a proven and mature encryption key management solution to VMware environments with a lower total cost of ownership. Townsend Security provides exactly the right solution and support for the Windows ISV and SI partner with their FIPS-140 certified Alliance Key Manager HSM appliance.
Encryption keys can be stored on the HSM device in either of the following ways. Key Managers actually do full key lifecycle management with protections built around distribution and storage inside and outside the HSM. HSM as a Service is cloud-neutral and supports heterogeneous cloud environments.
HSMs and Key Management. HSMs are built to protect cryptographic keys. AWS CloudHSM is a cloud-based hardware security module HSM that enables you to easily generate and use your own encryption keys on the AWS Cloud.
Hardware security modules act as trust anchors that protect the cryptographic infrastructure of some of the most security-conscious organizations in the world by securely managing processing and storing cryptographic keys inside a hardened tamper-resistant device. This enables you to take advantage of the wealth of services offered by these providers yet have a single centralized method of managing encryption. Single centralized encryption key management.
With CloudHSM you can manage your own encryption keys using FIPS 140-2 Level 3 validated HSMs. The latest generation of Key Managers however is starting to close the gap. Not so much with an HSM as it typically puts keys in one Security.
An HSM essentially creates and protects those keys and has limitations to the full lifecycle management of those keys outside of the HSM. Cloud key managers have not been keen to adopt standards such as the Key Management Interoperability Protocol KMIP. Large-sized banks or corporate offices often operate a variety of HSMs concurrently.
External Key Management services have been slow to answer the problem with their focus on the internal data center. Azure Key Vault Managed HSM is a cloud service that safeguards encryption keys. The use of HSM is a requirement for compliance with American National Standards Institute ANSI TG-3 PIN protection and key management guidelines as well as most card association and.
It complements services offered by leading cloud service providers like AWS Azure Google IBM and Oracle. An HSM will guard encryption keys through every stage of their lifecycle including creation import. Key management systems control and update these keys according to internal security policies and external standards.
The HSM solution must be easy to deploy using standard Windows development practices and offer the highest level of compliance assurance. Configure HSM Key Management. You can generate use rotate and.
The HSM provides an extensive range of functions including support for key management PIN generation encryption and verification and Message Authentication Code MAC generation and verification. After the Vault has been installed and has started successfully you can move the Server key to the HSM where it will be stored externally as a non-exportable key. A key management hardware security module HSM with NIST FIPS 140-2 compliance.
By leveraging the REST interfaces provided by cloud providers Key Managers can enable Bring Your Own-Key. A hardware security module HSM is a dedicated crypto processor that is specifically designed for the protection of the crypto key lifecycle.
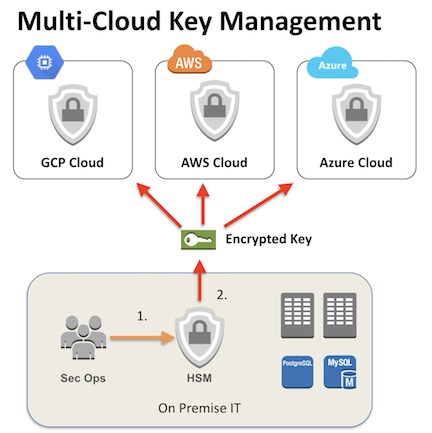 Multi Cloud Key Management Service And Deployment Options Thales
Multi Cloud Key Management Service And Deployment Options Thales
 Cloud Hsm Our Secure Key Management Approach
Cloud Hsm Our Secure Key Management Approach
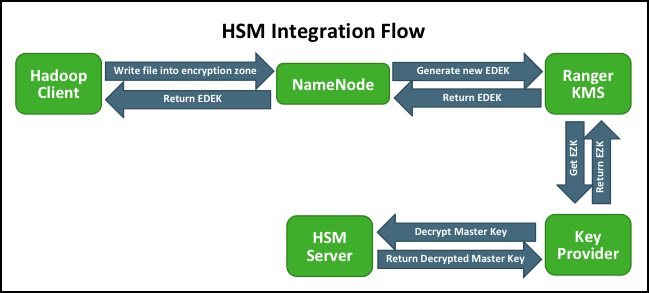 Store Master Key In A Hardware Security Module Hsm
Store Master Key In A Hardware Security Module Hsm
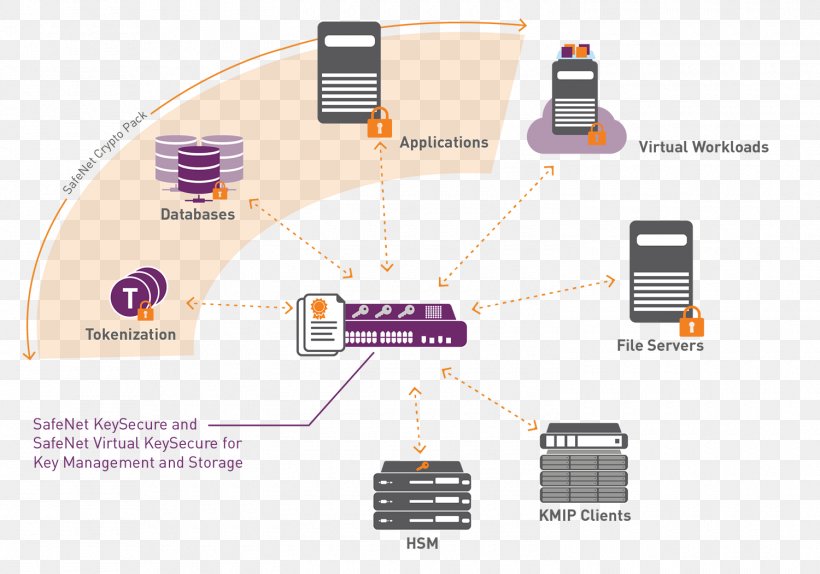 Safenet Key Management Hardware Security Module Cryptography Png 1500x1050px Safenet Authentication Computer Security Computer Software Cryptography
Safenet Key Management Hardware Security Module Cryptography Png 1500x1050px Safenet Authentication Computer Security Computer Software Cryptography
 Payment Encryption Key Management System Prime Factors
Payment Encryption Key Management System Prime Factors
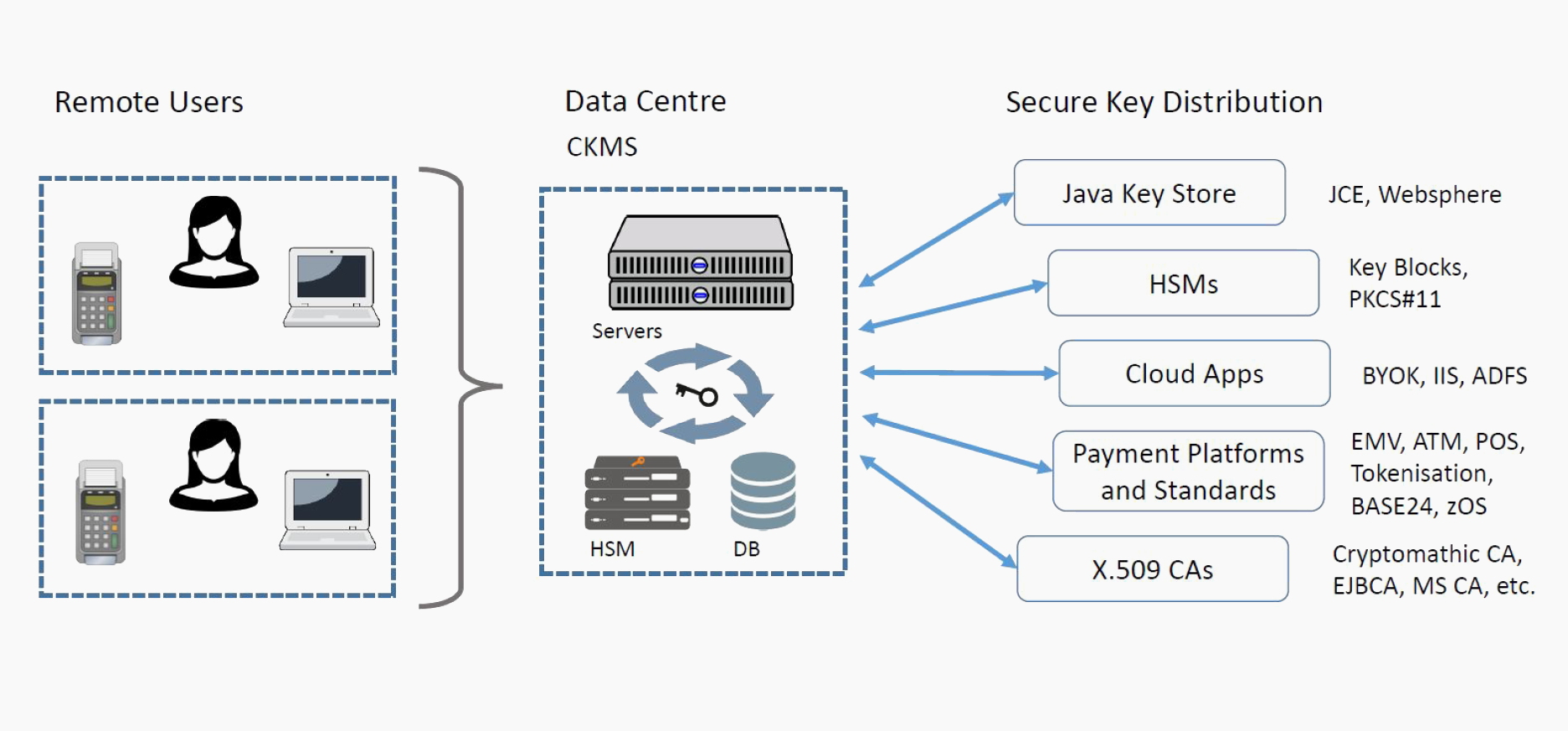 The Benefits Of An Automated And Centralized Key Management System
The Benefits Of An Automated And Centralized Key Management System
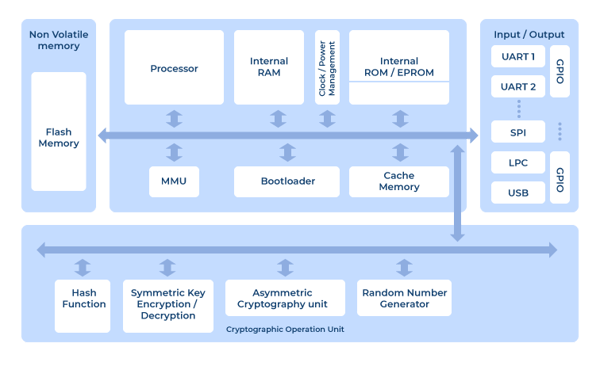 How Does Hardware Security Module Hsm Protect Payment Card Data
How Does Hardware Security Module Hsm Protect Payment Card Data
 Encryption Key Management Software Virtru
Encryption Key Management Software Virtru
 Why Can T Hsm And Key Management Be Provided To You As A Managed Service Or Can They By Fortanix Medium
Why Can T Hsm And Key Management Be Provided To You As A Managed Service Or Can They By Fortanix Medium
 Why Can T Hsm And Key Management Be Provided To You As A Managed Service Or Can They
Why Can T Hsm And Key Management Be Provided To You As A Managed Service Or Can They
Gemalto Safenet Keysecure Telecommunications Security Systems Limited




No comments:
Post a Comment
Note: Only a member of this blog may post a comment.