What is a Cyber Kill Chain. The cyber kill chain developed by Lockheed Martin is an industry-accepted methodology for understanding how an attacker will conduct the activities.
 Lockheed Martin Cyber Kill Chain Ckc 22 Seven Steps The Part That Download Scientific Diagram
Lockheed Martin Cyber Kill Chain Ckc 22 Seven Steps The Part That Download Scientific Diagram
What is a Kill Chain.

Cyber kill chain. The biggest criticism of this framework is that it does not consider modern attacks. Ad Explore new cybersecurity trends technologies and approaches. 2017 Deloitte Touche Tohmatsu Limited Cyber 101.
Ad Unlimited access to Cyber Security market reports on 180 countries. The cyber kill chain is essentially a cybersecurity model created by Lockheed Martin that traces the stages of a cyber-attack identifies vulnerabilities and helps security teams to stop the attacks at every stage of the chain. The Intrusion Kill Chain is a kill chain specifically focused on a cybersecurity intrusion.
The purpose of the model is to better understand the stages an attack must go through to conduct an attack. Each stage demonstrates a specific goal along the attackers path. The Cyber Kill Chain was developed by Lockheed Martin as a framework to help organizations understand the process of cyber attacks.
Download Reports from 10000 trusted sources with ReportLinker. Together we can make networks devices and applications more secure. Ad Explore new cybersecurity trends technologies and approaches.
The cyber kill chain is a series of steps that trace stages of a cyberattack from the early reconnaissance stages to the exfiltration of data. The model identifies what the adversaries must complete in order to achieve their objective. The term kill chain is adopted from the military which uses this term related to the structure of an attack.
The cyber kill chain CKC is a classic cybersecurity model developed by the computer security incident response CSIRT team at Lockheed Martin. The kill chain helps us understand and combat ransomware security breaches and advanced persistent attacks APTs. A kill chain is a system to procedurally target engage and neutralize an adversary.
For example most phishing attacks ignore the fourth stage and rely on the victim. Together we can make networks devices and applications more secure. If you understand every point in the chain of events of a cyber-attack you can focus your efforts on breaking that chain and mitigating the damages.
While the Cyber Kill Chain sets a good baseline for self-defense it has limitations. Supplementary Reading Slide 2 The cyber kill chain is a sequence of stages required for an attacker to successfully infiltrate a network and exfiltrate data from it. Download Reports from 10000 trusted sources with ReportLinker.
Developed by Lockheed Martin the Cyber Kill Chain framework is part of the Intelligence Driven Defense model for identification and prevention of cyber intrusions activity. Ad Unlimited access to Cyber Security market reports on 180 countries.
 What Are The Different Phases In A Successful Cyber Kill Chain
What Are The Different Phases In A Successful Cyber Kill Chain
 Eventtracker Enterprise And The Cyber Kill Chain Netsurion
Eventtracker Enterprise And The Cyber Kill Chain Netsurion
 What Is A Cyber Kill Chain And How It Works Stages And Examples
What Is A Cyber Kill Chain And How It Works Stages And Examples
 Cyber Kill Chain Cyber Attack Cyber Lockheed
Cyber Kill Chain Cyber Attack Cyber Lockheed
 The Unified Kill Chain Part 2 Mitigate Cyber
The Unified Kill Chain Part 2 Mitigate Cyber
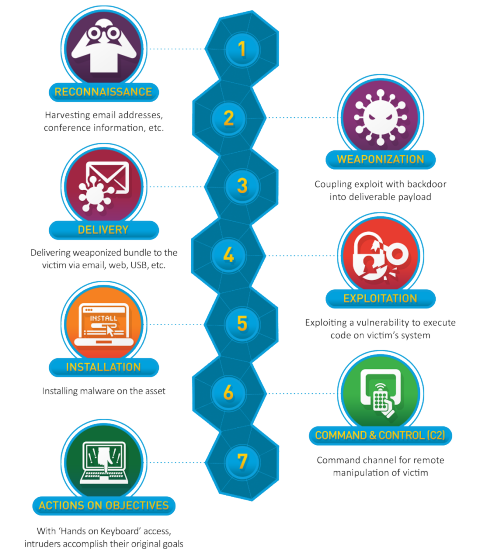 Cyber Kill Chain Lockheed Martin
Cyber Kill Chain Lockheed Martin
 What Is A Cyber Kill Chain And How It Works Stages And Examples
What Is A Cyber Kill Chain And How It Works Stages And Examples
 What Is The Cyber Kill Chain And How To Use It Effectively Varonis
What Is The Cyber Kill Chain And How To Use It Effectively Varonis
 What Is The Cyber Kill Chain And How To Use It Effectively Varonis
What Is The Cyber Kill Chain And How To Use It Effectively Varonis
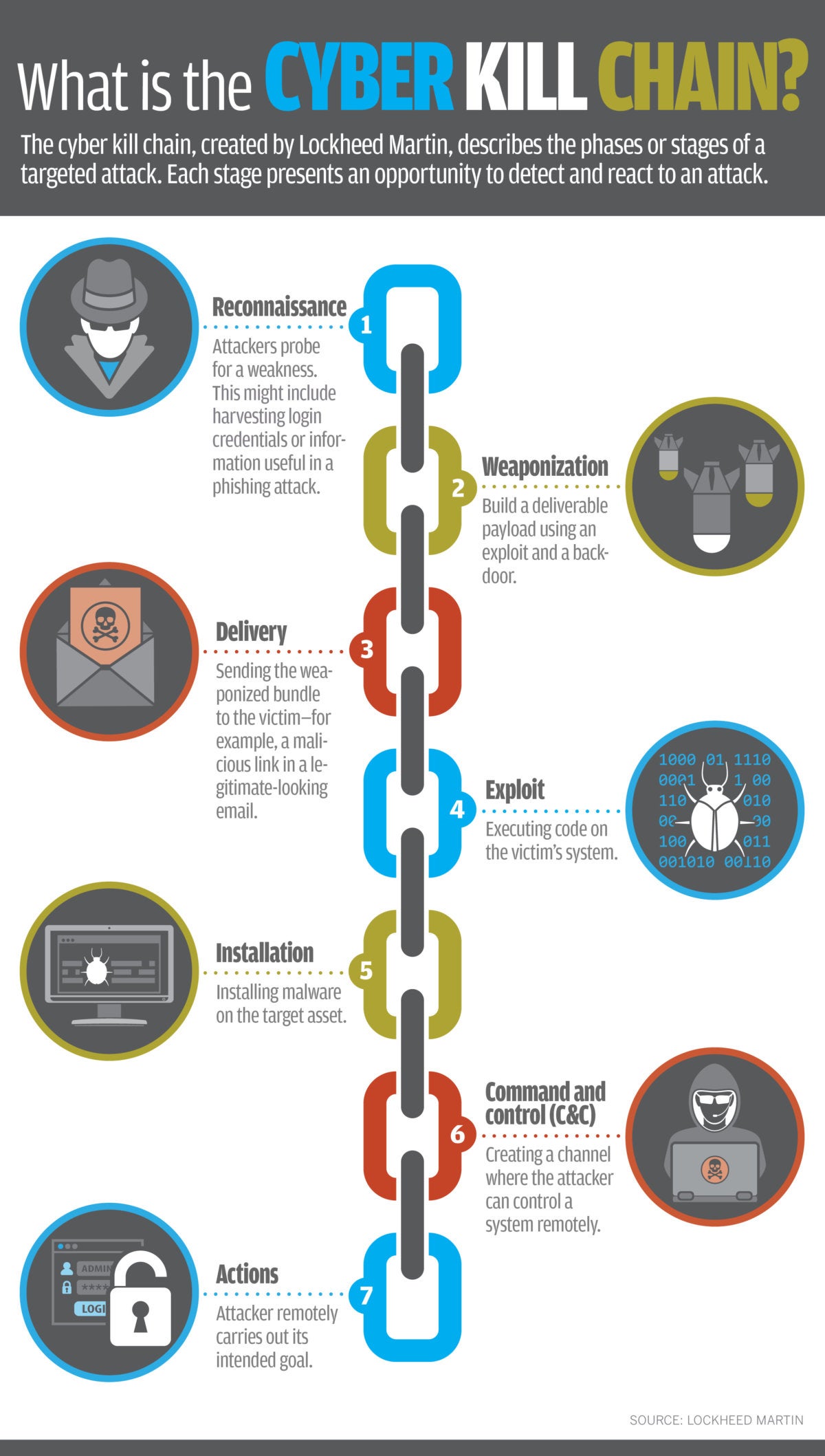 What Is The Cyber Kill Chain Why It S Not Always The Right Approach To Cyber Attacks Cso Online
What Is The Cyber Kill Chain Why It S Not Always The Right Approach To Cyber Attacks Cso Online
 The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
The Importance Of Endpoint Security In Breaking The Cyber Kill Chain
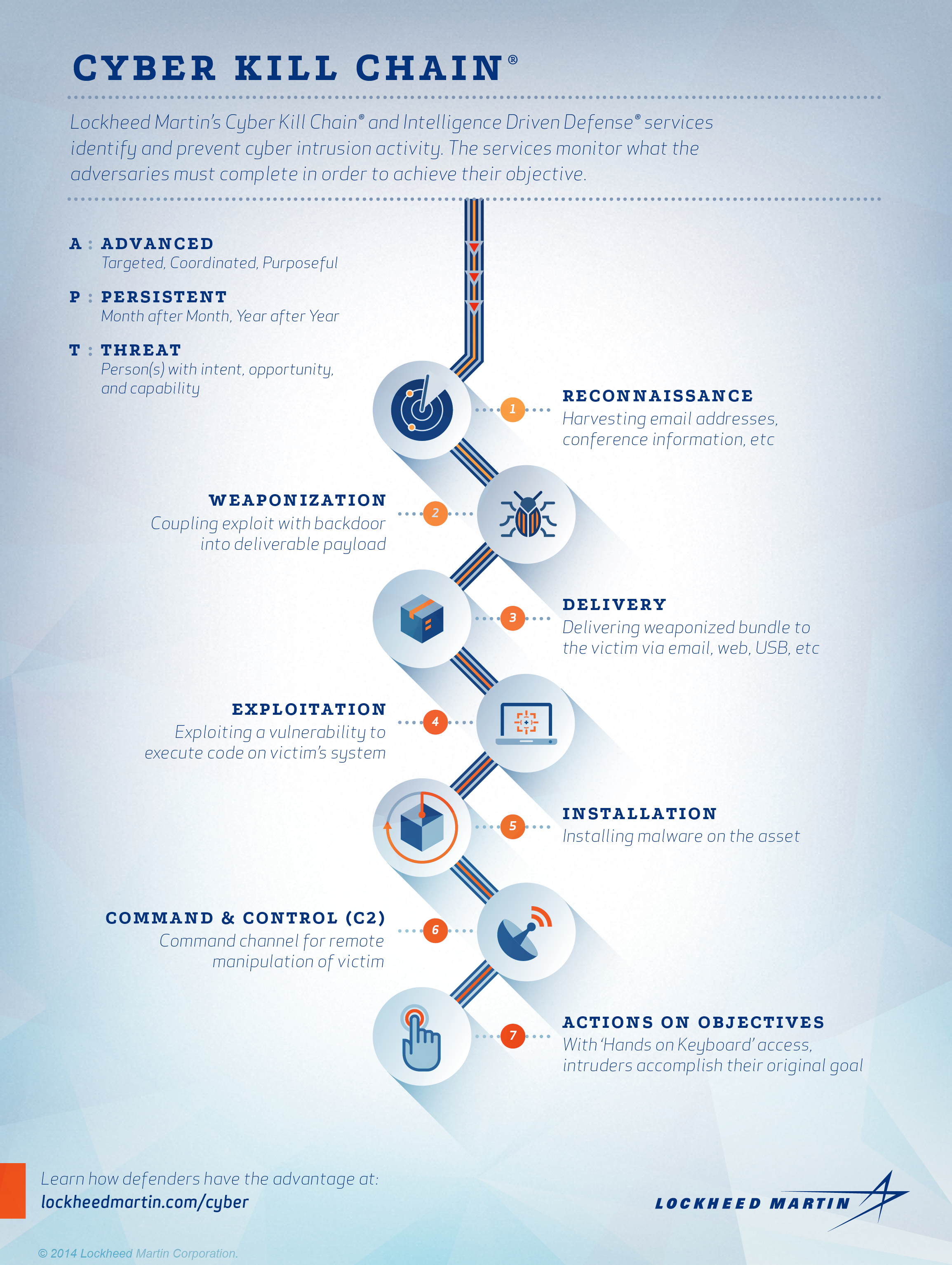 Leveraging The Human To Break The Cyber Kill Chain
Leveraging The Human To Break The Cyber Kill Chain

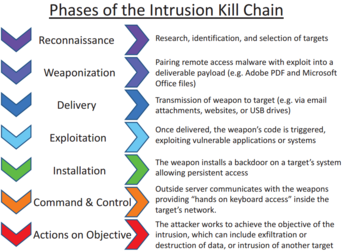

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.