Vulnerability management market dynamics and use cases. These include unsecure system configurations or missing patches as well as other security-related updates in the systems connected to the enterprise network directly remotely or in the cloud.
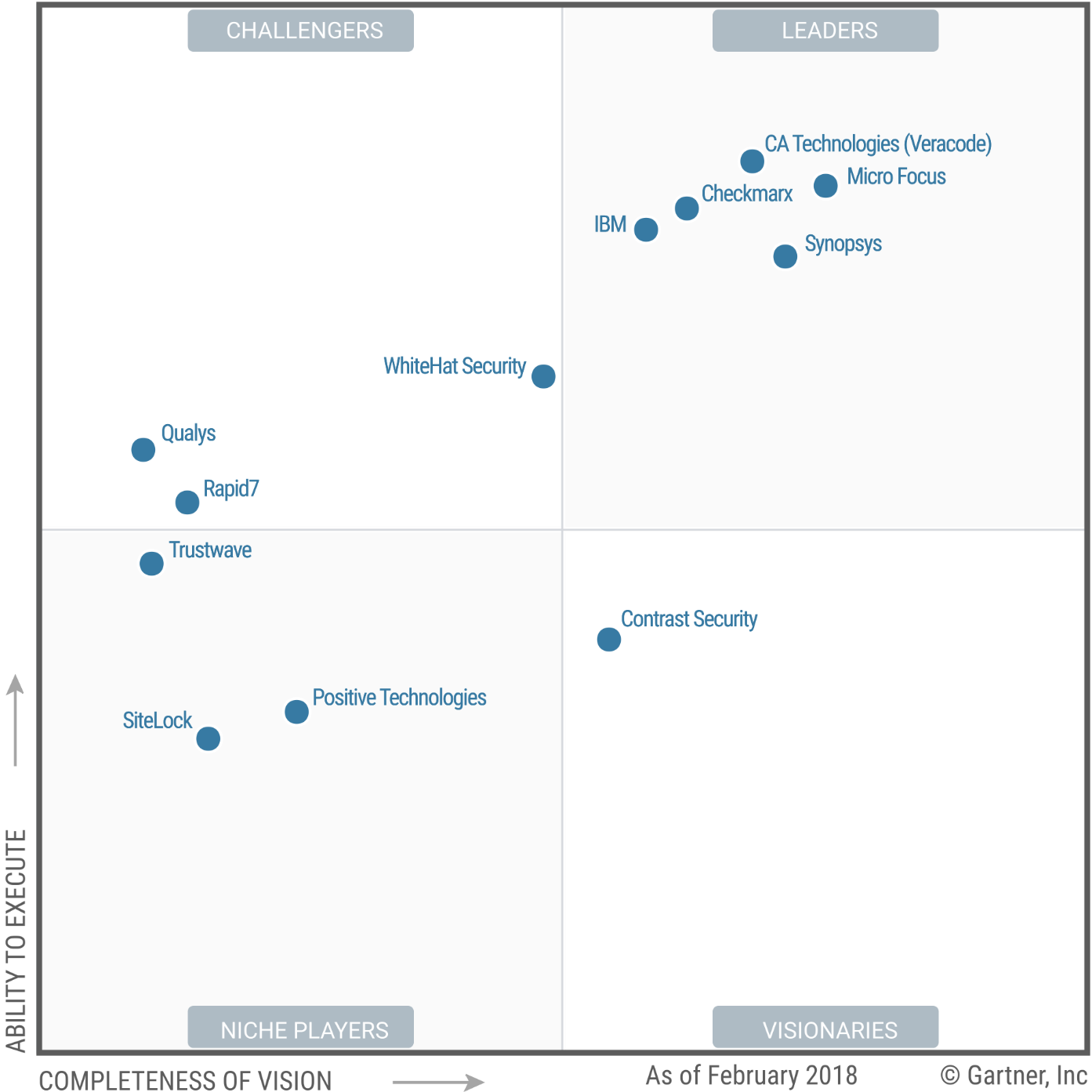 Ibm Sustains A Leadership Position In 2018 Gartner Magic Quadrant For Application Security Testing
Ibm Sustains A Leadership Position In 2018 Gartner Magic Quadrant For Application Security Testing
Tools are only now being expanded to cover in-depth security configuration assessment SCA large-scale vulnerability prioritization and new.
Gartner vulnerability management. However many organizations have problems optimizing their programs to achieve desired results. Read it today to learn about. It analyzes members viewpoints on various aspects of these programs types of assets resourcing strategies and organizational models.
The Future of Vulnerability Management is Risk-Based is published by Kenna Security. It focused on a risk-based approach for a vulnerability management. Vulnerability management including vulnerability assessment represents a proactive layer of enterprise threat defense.
The vulnerability assessment VA market is made up of vendors that provide capabilities to identify categorize and manage vulnerabilities. Vulnerability management is a critical security process. Editorial content supplied by Kenna Security is independent of Gartner analysis.
Gartner is a registered trademark of Gartner. Ad Search for results at Life123. VM remains very challenging to many organizations and this guidance presents a structured approach to VM best practices for technical professionals focused on security.
All Gartner research is used with Gartners permission and was originally published as part of Gartners syndicated research service available to all entitled Gartner clients. Analyst firm Gartner recently published a report titled Implement a Risk-Based Approach to Vulnerability Management. It includes threat and vulnerability management endpoint detection and response EDR incident response and alert analysis advanced hardening tools and monitoring and reporting.
The VM module is relatively easy to setup and allows you to perform both internal and external vulnerability assessment against your assets. Vulnerability management is a critical security process. For more on Gartners perspective on risk-based vulnerability management download this complimentary copy of Gartners latest Market Guide for Vulnerability Assessment.
Ad Search for results at Life123. SRM leaders should run vulnerability management continuously to reduce the threats against their organizations. You can also configure authenticated scans.
Discover Prioritize Remediate Vulnerabilities. Vulnerability management is arguably the best proactive thing you could be doing in your security operations. However many security and risk management leaders have problems optimizing their programs to achieve desired results.
Ad Automated Patch management. Strategic vision for vulnerability management. Vulnerability management Security Operations for Technical Professionals After a huge delay I can finally announce that the new version of our Vulnerability Management Guidance Framework is out.
Although it is a refresh of a document that has gone through many updates even before my Gartner time this one has some very nice new stuff to mention. The summary also highlights the extent of automation in members vulnerability management programs. Gartner named Microsoft a Leader for Endpoint Protection Platforms recognizing our products and our strengths and ability to execute and completeness of vision.
Not so long time ago Gartners report Vulnerability Management an essential piece of the security puzzle has become publicly available. Craig Lawson VP analyst at Gartner offered the following key takeaways. Vulnerability assessment VA plays a critical role in enterprise vulnerability management VM.
At the bottom of the document there is a reference to Gartner. Now you can read it for free by filling out a questionnaire on F-Secure website. Read Gartners Market Guide for Vulnerability Assessment to understand the breadth of vulnerability risk management capabilities available today get insights that will help you navigate vendor offerings and see why vulnerability prioritization is key to reducing cyber risk.
Ad Automated Patch management. Recommendations for leaders responsible for security operations and vulnerability management. Find your search here.
The Qualys vulnerability management solution is a solid and mature enterprise class solution. Find your search here. Finds Real SQL Injection XSS Vulnerabilities.
Discover Prioritize Remediate Vulnerabilities. Finds Real SQL Injection XSS Vulnerabilities. 2019 Gartner Inc.
Gartner A Guide To Choosing A Vulnerability Assessment Solution 2019
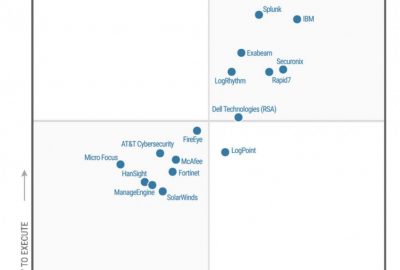
 2020 Gartner Magic Quadrant For Siem Rapid7 Named A Leader Rapid7 Blog
2020 Gartner Magic Quadrant For Siem Rapid7 Named A Leader Rapid7 Blog
 Boost Security With These Gartner Recommended Projects Qualys Security Blog
Boost Security With These Gartner Recommended Projects Qualys Security Blog
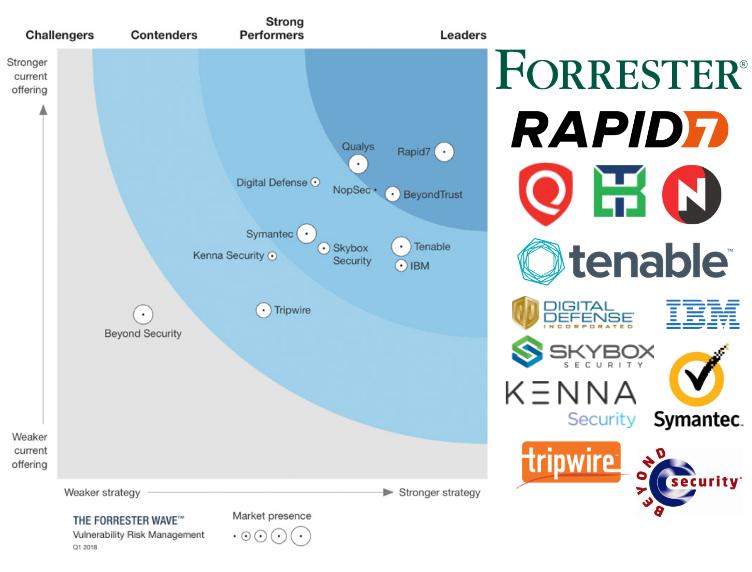 My Short Review Of The Forrester Wave Vulnerability Risk Management Q1 2018 Alexander V Leonov
My Short Review Of The Forrester Wave Vulnerability Risk Management Q1 2018 Alexander V Leonov
 The New Vulnerability Management Guidance Framework Augusto Barros
The New Vulnerability Management Guidance Framework Augusto Barros
 2017 Gartner Magic Quadrant For Siem
2017 Gartner Magic Quadrant For Siem
Gartner Market Guide For Vulnerability Management
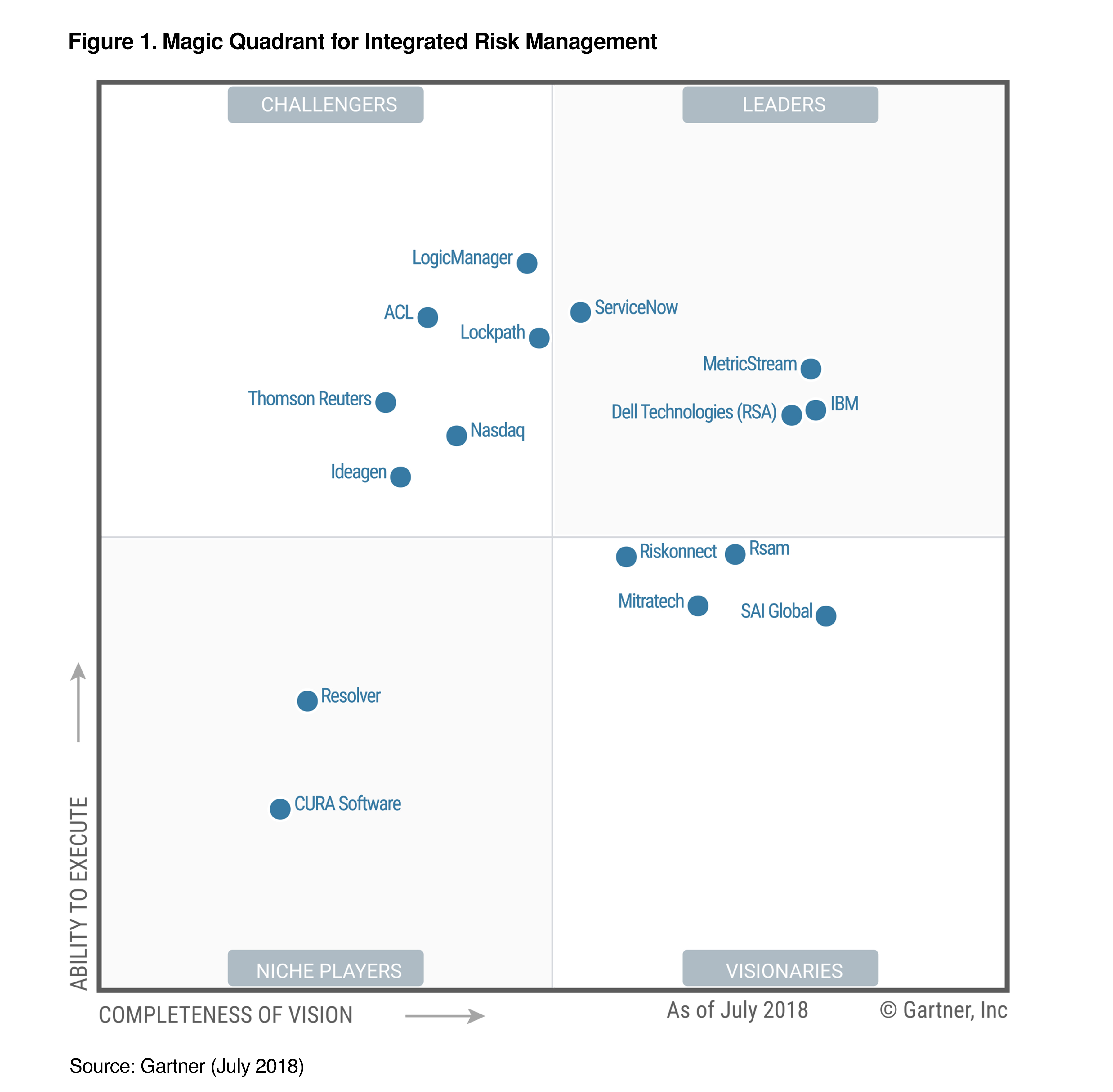 Servicenow Named A Leader In Gartner Magic Quadrant For Integrated Risk Management Business Wire
Servicenow Named A Leader In Gartner Magic Quadrant For Integrated Risk Management Business Wire
Trend Micro Tippingpoint Named A Leader In 2017 Gartner Magic Quadrant For Intrusion Detection And Prevention Systems Idps
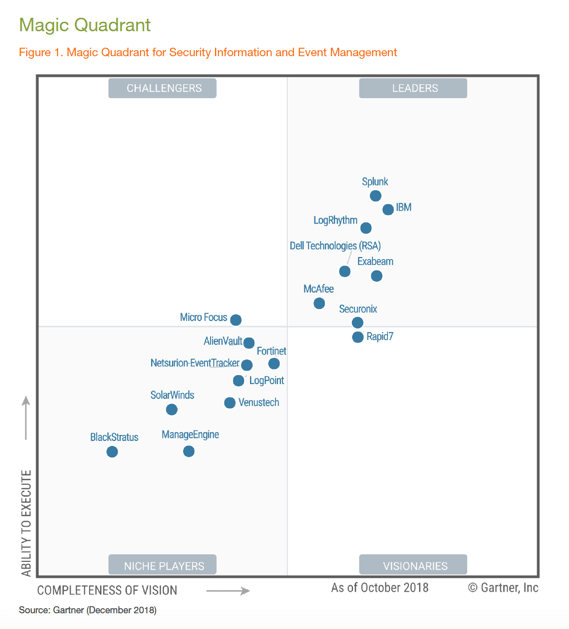 Logrhythm Named A Leader In The 2018 Gartner Siem Magic Quadrant Logrhythm
Logrhythm Named A Leader In The 2018 Gartner Siem Magic Quadrant Logrhythm
 Gartner Magic Quadrant Vulnerability Management Page 1 Line 17qq Com
Gartner Magic Quadrant Vulnerability Management Page 1 Line 17qq Com
 It Vendor Risk Management 2019 Gartner Magic Quadrant I Surecloud Inc
It Vendor Risk Management 2019 Gartner Magic Quadrant I Surecloud Inc
 Gartner Magic Quadrant Vulnerability Management Page 1 Line 17qq Com
Gartner Magic Quadrant Vulnerability Management Page 1 Line 17qq Com

No comments:
Post a Comment
Note: Only a member of this blog may post a comment.