There are huge piles of data on file systems file shares and collaboration systems like SharePoint which are all but unknown to the security world. It enables them to meet regulatory requirements by providing proof of compliance during audits and increase staff productivity by reducing time spent on diagnostics forensics and data administration tasks.
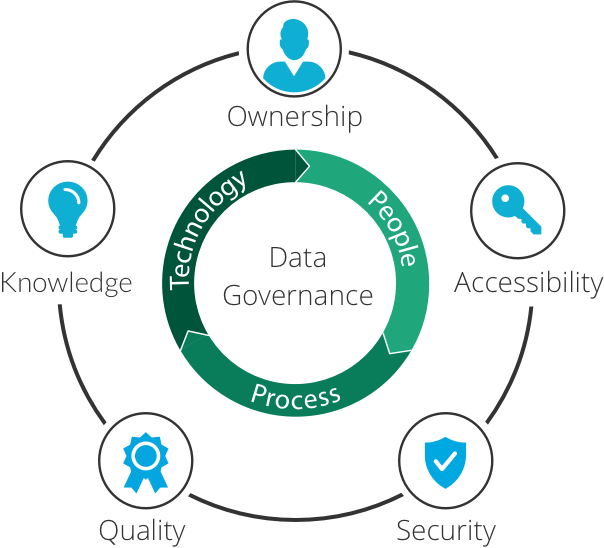 What Is Data Governance Frameworks Tools Best Practices Imperva
What Is Data Governance Frameworks Tools Best Practices Imperva
Establish an access request workflow such as a request portal so users can easily request access to data they need to do their jobs.

Data access governance. Saviynts Data Access Governance DAG helps you discover analyze protect and manage access to all of your data structured or unstructured regardless of whether your IT ecosystem is on-premises hybrid or cloud-based. Though every time I ask about Data Access Governance every single security professional and everyone else in IT for. Remediate access issues with ease No rules no document tagging by end users.
The majority of corporate data is now stored in file-sharing services like Box SharePoint and Google Drive. Certifications are delivered directly to data owners which lets them see who currently has access to their data and make changes without any involvement from IT. For example a useful report with the SQL to implement or a way to achieve some advanced rule processing.
Data Access Governance DAG is a broad term that refers to way we govern access to our data if you havent already figured that out. This means managing access to these systems is critical especially as hacker attacks on these services continue to increase. Audit the actions of data owners to be sure that all operations are authorized.
DAG - Data Access Governance DAG is a data security technology that allows enterprises to gain visibility to sensitive unstructured data that exists across the organization and enforce policies to control access to that data. Put more data to work with Talends unified platform built for the cloud. Data Access Governance DAG is securitys big unaddressed to-do item.
Netwrix helps enable strong data access governance DAG across your file servers as well as collaboration systems like SharePoint and SharePoint Online by giving you deep insight into your unstructured data including information about possible security. Data access governance DAG is a business-oriented solution that helps organizations find and protect sensitive unstructured data. Unstructured data consists of human-generated files spreadsheets presentations PDFs etc.
Dynamic monitoring and governance of access rights to sensitive data Monitor for inappropriate sharing permissions or location or classification that could be in violation of regulatory and compliance requirements without any pre-defined rules. With Lepide you have a complete solution that enables you to identify where your sensitive data is get detailed analysis and alerts on user behavior and ensure access rights by analyzing permissions to your unstructured data and reversing unwanted changes. Make sure that access to groups distribution lists and sensitive business data is consistently reviewed by the right people.
Secure and protect access to sensitive data. Data owners located in the specialist departments autonomously control their access without direct intervention of the IT department. Audit and report on access to sensitive data as well as changes to it.
Ad Bring productivity collaboration and security to data workers. Empower data owners to control access rights to the data they own. Monitoring and control of access rights to unstructured data Secure management of information authorizations and resources in systems containing unstructured data.
Data Access Governance involves carrying out risk assessments implementing privacy policies discovering and classifying sensitive data setting up access controls and monitoring access to critical assets. Data Access Governance Solution. Data Access Governance Immuta helps data engineers and DataOps teams automate data governance security access control and privacy protection for modern cloud-native analytics platforms.
Additionally major compliance regulations. RSA Identity Governance LIfecycle recipes is a collection of items to help you get the most out of your product deployment. Ad Bring productivity collaboration and security to data workers.
Put more data to work with Talends unified platform built for the cloud. Identify All Access to All Data Automate Data Access Risk Analysis Establish Risk-Based Data Access Policies. Data Access Governance DAG Documentation and Con.
Assign each group appropriate access to shared data.
 Techtalk Data Access Governance Done Right
Techtalk Data Access Governance Done Right
 Prioritizing Data Access Governance Initiatives Through Discovery
Prioritizing Data Access Governance Initiatives Through Discovery
 3 Data Access Governance Econet English
3 Data Access Governance Econet English
 Role Based Access Control And Governance Imprivata
Role Based Access Control And Governance Imprivata
 Bankrupt Retailer Customer Deposit Consignment Inventory
Bankrupt Retailer Customer Deposit Consignment Inventory
 Rsa Data Access Governance Youtube
Rsa Data Access Governance Youtube
 5 Challenges With Combining Data Access Governance And Iam
5 Challenges With Combining Data Access Governance And Iam
 What Is Data Access Governance Youtube
What Is Data Access Governance Youtube
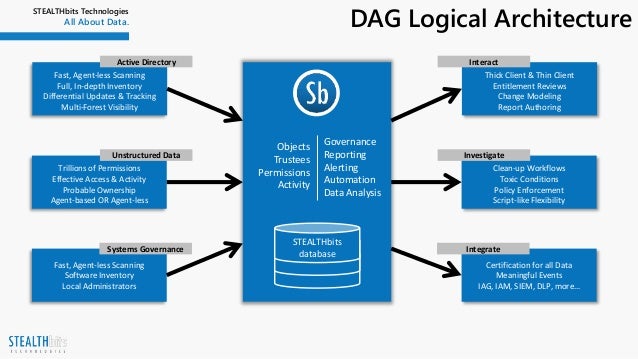 Smp For Data Access Governance
Smp For Data Access Governance

 Data Access Governance The Best Medicine Netgovern
Data Access Governance The Best Medicine Netgovern
 Data Governance Gip Digital Watch
Data Governance Gip Digital Watch
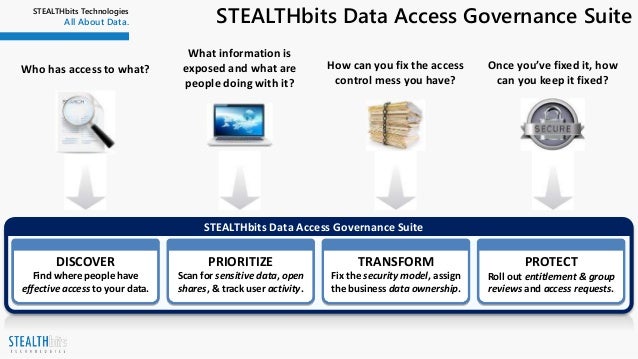 Smp For Data Access Governance
Smp For Data Access Governance


No comments:
Post a Comment
Note: Only a member of this blog may post a comment.