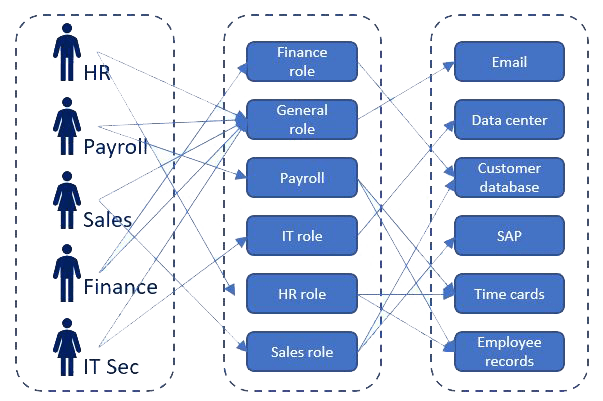
One of the main goals of RBAC is to ensure employees are only granted the necessary level of access to perform their job. Align the roles with employees within your organization.
 Cissp Certification Rbac Role Based Access Control Thorteaches Cissp Cism Pmp Training
Cissp Certification Rbac Role Based Access Control Thorteaches Cissp Cism Pmp Training
Avoid creating too many roles as in this case you will defeat the purposed and run a risk of creating a user-based access control instead of RBAC.
Role based access control best practices. Role-based access control allows you to improve your security posture comply with relevant regulations and reduce operational overhead. This article describes some best practices for using Azure role-based access control Azure RBAC. As such IGA solutions must be flexible in supporting the role concepts required by each application.
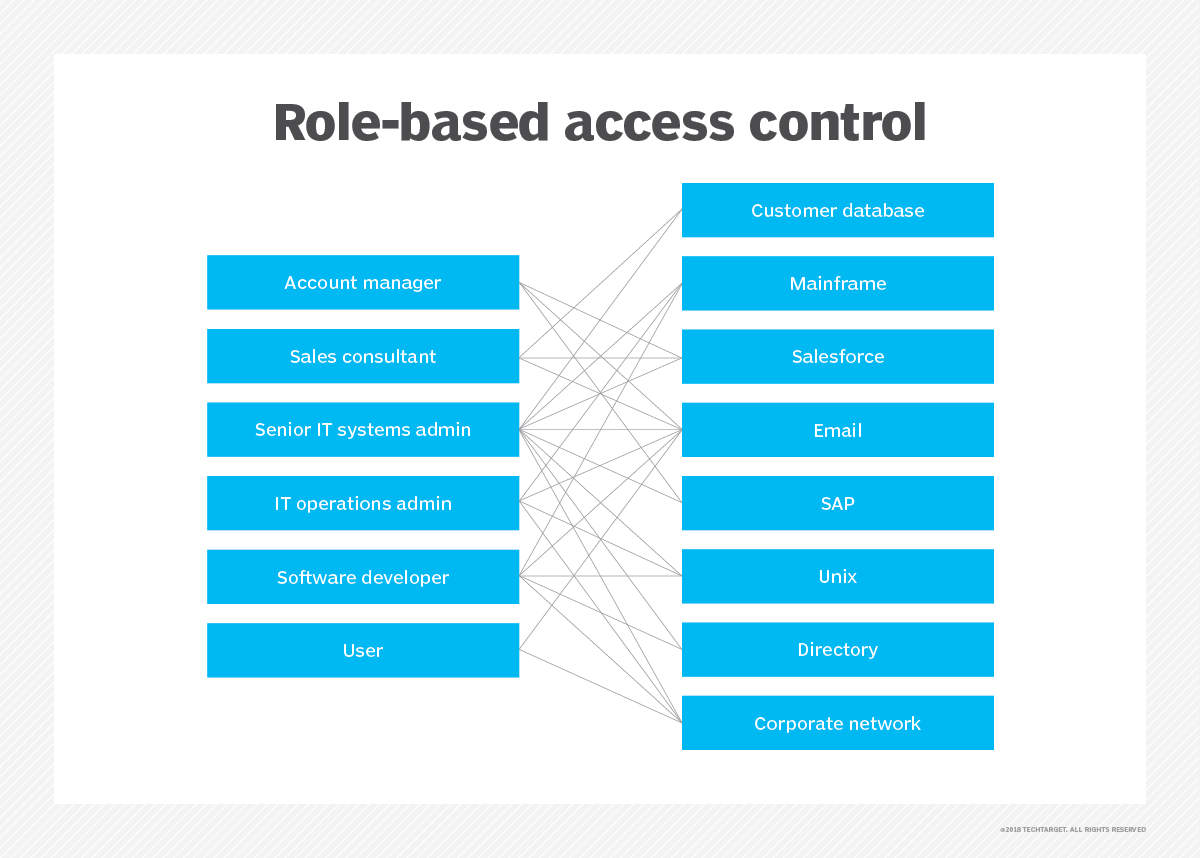
Of duties job rotation mandatory access control discretionary access control role based access control and rule based access controls are most commonly used. Role-based access control RBAC is a system based on the roles of individual users within an organization to control network access. Role Based Access Control.
Minimize the volume of security data. Role-Based Access Controls RBAC Users need privilege to be able to do their jobs but root or local admin access is far more than they need and assigning them creates unnecessary security risks. RBAC requires workers to have access rights only to the data they use to do their job and forbids them from accessing data that is not important to them.
Developing Business Roles and Technical Roles Applications often use roles to delegate organizational tasks andor rights to users and each application has its own requirements for role management. What are best practices for implementing RBAC. In addition industry standards have been established both by government and private entities to identify best practices.
Keep track of important operations. Role-based access control - best practices Create exclusive custom groups update user permissions based on specific job attributes and new memberships Create custom groups of computers based on departments job titles etc. Role Based Access Control is an approach that uses the job functions performed by individual users within the organization to determine their appropriate access levels.
These best practices are derived from our experience with Azure RBAC and the experiences of customers like yourself. Define data and resources to which access should be limited. Using Azure RBAC you can segregate duties within your team and grant only the amount of access to users that they need to.
5 steps to simple role-based access control RBAC RBAC is the idea of assigning system access to users based on their role in an organization. Carefully choose the granularity of access rights. Role Based Access Control is an approach that uses the job functions played by individual users within the organization to determine what access they should have.
Best Practices for Role Based Access Control. Create roles with the same access needs. Only grant the access users need.
Prefer to open doors rather than to close them. Role-based access control best practices can be achieved following these steps. One of the main goals of RBAC is to grant employees only the access they need to do their jobs and to prevent them from having access that is not relevant to them.
However implementing role-based access control across an entire organization can be complex and can result in pushback from stakeholders. Remove application silos and unify access control. Its important to remember that not every employee.
Separate access logic from business logic.